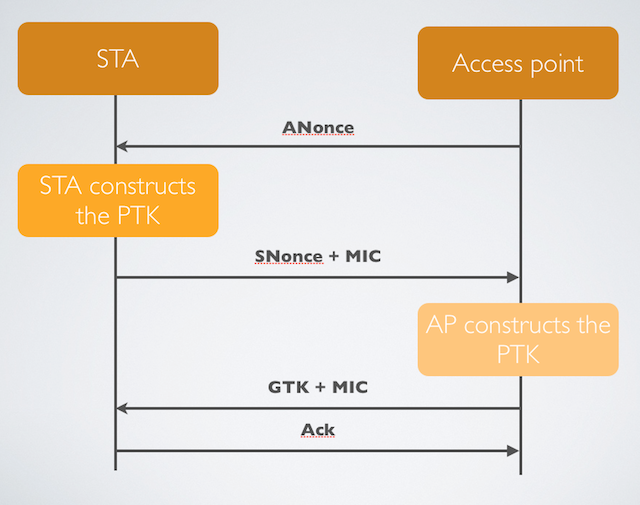
How to Hack Wi-Fi: Creating an Evil Twin Wireless Access Point to Eavesdrop on Data « Null Byte :: WonderHowTo

This Twenty-Year Old Hack Still Beats Most Wi-Fi Access Points – And Here's Why - Secplicity - Security Simplified

WiFi hacking devices. (a) Pocket-size WiFi attack tool. (b) Rogue WiFi... | Download Scientific Diagram

Wireless Hacking: Projects for Wi-Fi Enthusiasts: Cut the cord and discover the world of wireless hacks! by Lee Barken | eBook | Barnes & Noble®

Is there any appropriate method for hacking wifi? I used many tricks but none of them are correct. - Quora

How to Hack Wi-Fi: Creating an Invisible Rogue Access Point to Siphon Off Data Undetected « Null Byte :: WonderHowTo

How to Hack Wi-Fi: Get Anyone's Wi-Fi Password Without Cracking Using Wifiphisher | Wifi hack, Computer forensics, Wifi password